Cybersecurity

Featured Content
MFA for Remote Access

Important: Microsoft Authenticator Notification
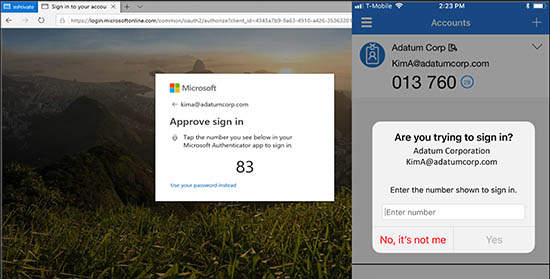
If you are using the Microsoft authenticator push notification for your multi factor authentication method you will be presented with a number on your screen to match the number on your phone. This was done to increase the security of the multifactor authentication. There have been several instances of MFA fatigue attacks, where bad actors are sending out multiple requests for access and these requests being accidently approved. By implementing number matching, users are prevented from accidentally approving MFA requests. The number will appear on the computer screen, and you will be required to enter the number into the authenticator app. For more information, please check out Microsoft’s website link below:
Featured Content
Why do I have to use the Microsoft Authenticator App for Remote Access?
The Microsoft Authenticator app is required because the ability to put in a username and password is only available during login. During the login process, our authentication server creates a push notification that goes to the Authenticator app. There is no place to accept codes from alternative apps or text messages. The Microsoft Authenticator app is required because we are using Microsoft Azure to provide the MFA services.


